‘I lost thousands in savings to the dark web while on holiday – and hackers are still targeting me’
Matthew Shaw was told he spent the money on a hotel in Romania and a bar tab

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.A teacher who lost thousands in savings while on holiday has issued a warning to others on the risk of hackers.
Matthew Shaw, a 27-year-old science teacher, was on holiday in Cornwall in August 2021 with his wife Davina, 27, who works in a nursery, and the couple were looking forward to the two-week trip as their only chance of the year to go away.
Mr Shaw was unaware his identity was sold on the dark web and lost £3,500 to a Romanian hacker who used it to pay for a hotel and drinks tab.
One day, while driving to try jet skiing for the first time, Matthew said he unexpectedly received a notification on his phone from his bank, telling him his account had just paid £3,500 for a hotel stay – although the location and name were not provided.
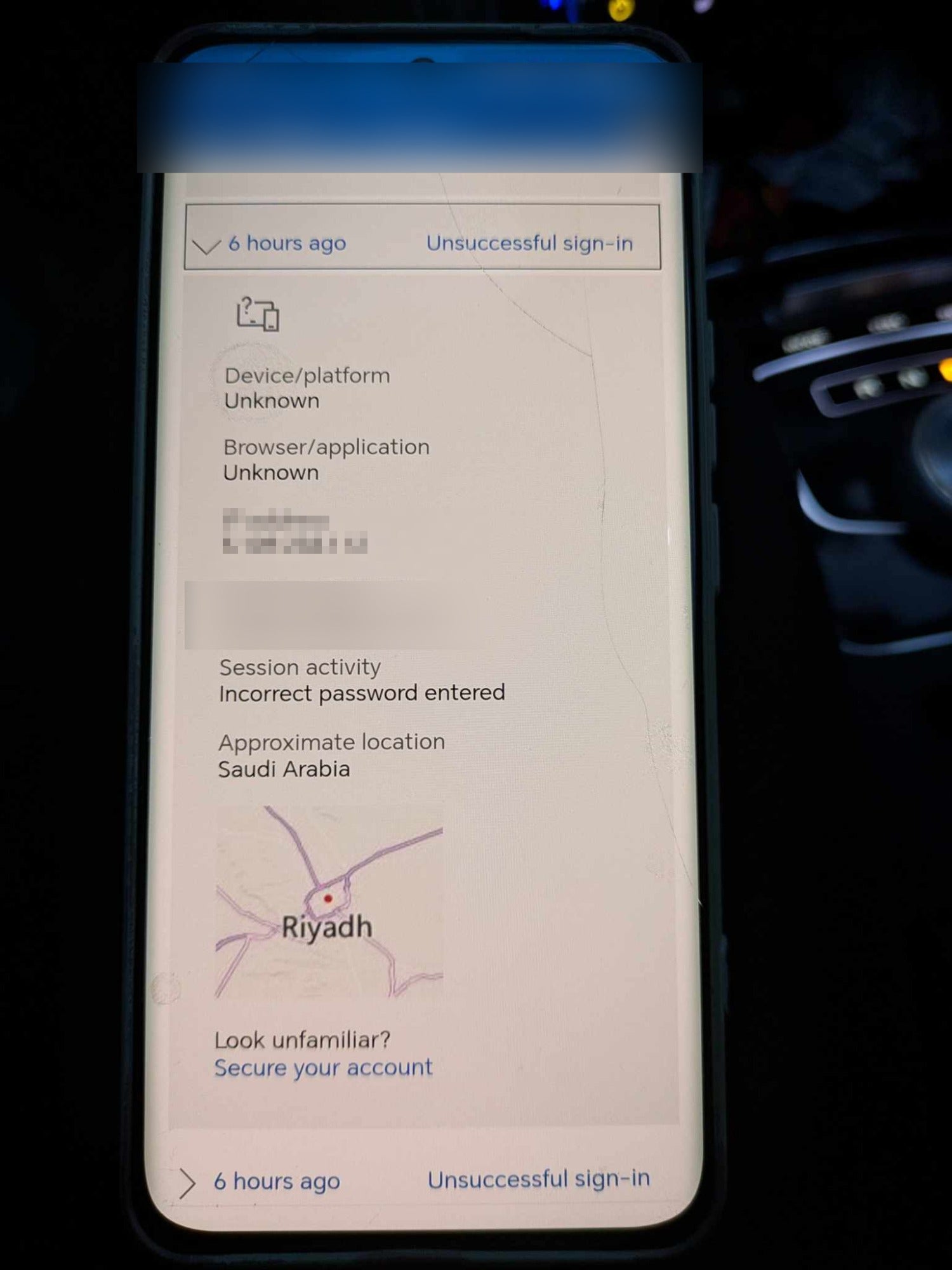
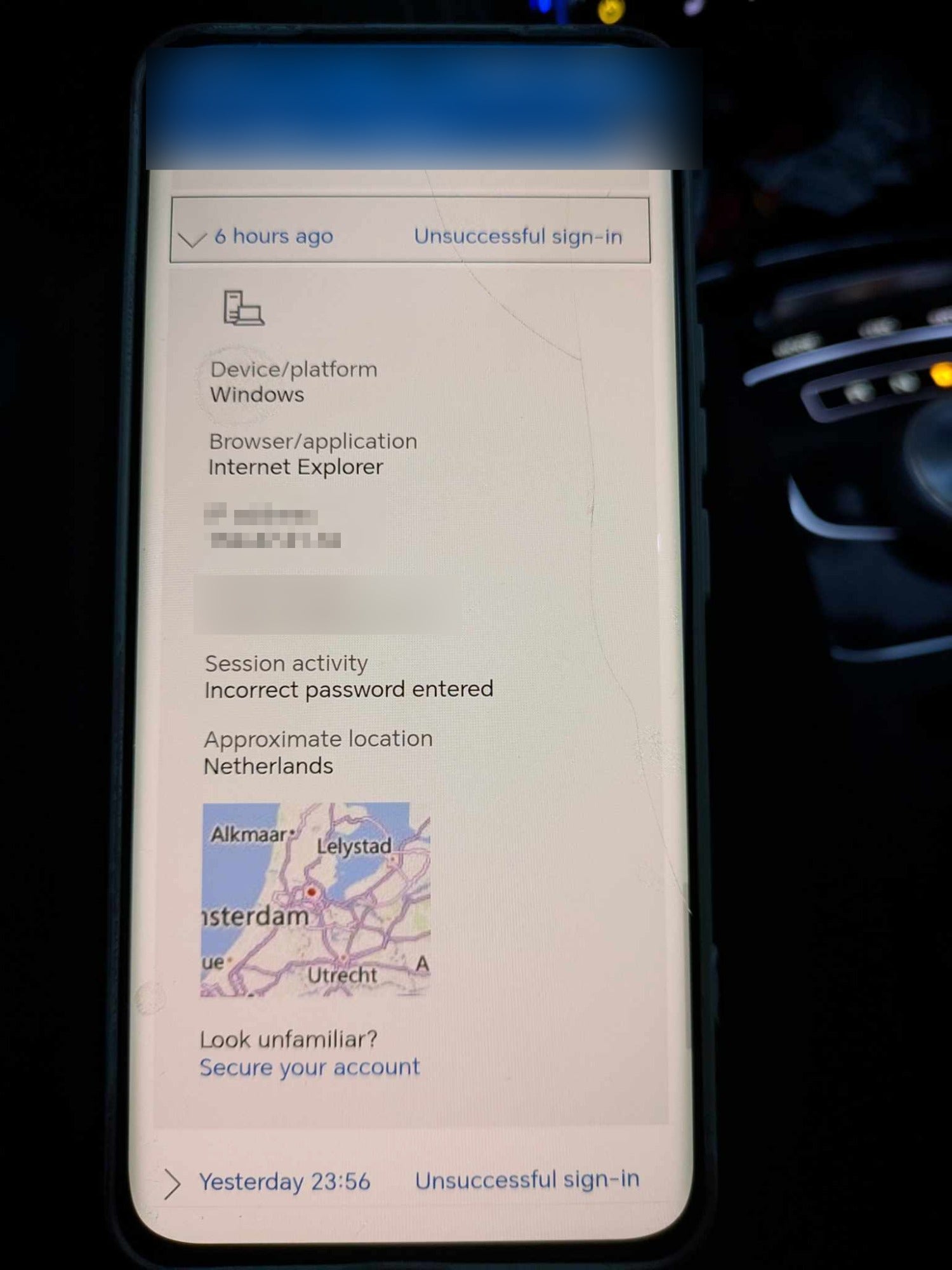
“Panicking”, Matthew said he called the bank, First Direct, which concluded that someone from Romania had opened an account in his name with Monese – a digital financial services company – using his identity and linked it to his First Direct account to pay for the hotel after finding his details on the dark web – which the company said could cost just 10 US dollars.
The £3,500 transaction left Matthew with just £20 in his bank account, and the couple from Bourton-on-the-Hill, Gloucestershire, had to end their holiday a week early, leaving Davina in tears.
Matthew said First Direct was “brilliant” and the money was refunded a week later, but even now, having tightened his security measures, he said he receives at least six or seven email notifications every day asking him to approve unauthorised sign-in attempts.
Speaking about the moment he received the notification on holiday, he told PA Real Life: “We had woken up, we had breakfast, and we were on our way to go and do jet skiing – something we’ve always wanted to do.
“Then, I parked up and I had a notification at the top of my phone saying, ‘£3,500 has been paid to a hotel’.
“I thought, ‘Oh my God, what is this?’, and I rang First Direct straight away and said, ‘This is not me’.
“They were going through their security questions, but I was just panicking and thinking, ‘All my money’s gone – that was our savings for a house and it’s all gone’.”
At the time, Matthew was an unqualified supervisor teacher.

He said his only opportunity to take leave over the summer was during the six-week school holiday period, and because Davina was “restricted” with her holiday allowance, the couple had planned their two-week camping trip in Cornwall thoroughly.
“We have that one holiday for the whole year and that’s it,” Matthew said.
The couple had booked tickets to visit a seal sanctuary and a crystal maze in Cornwall and were on their way to try jet skiing when Matthew received the notification.
“(First Direct) said my email had been hacked and a person in Romania had obtained my ID, set up a bank account using my ID, and then basically paid for a hotel with all the drinks and everything using my credentials, which then came out of my bank account,” he said.
“They said the process was that someone had hacked into my email, got my ID and everything, and then that was published to the dark web… and, apparently, you could pay 10 dollars to access someone’s information.”
Matthew said he is tech-savvy and had different passwords for all his accounts, and he regularly changed his email address, so he did not think he was vulnerable to identity theft.
But being left with just £20 in his account, the couple had to cut their trip short and ask for refunds for their upcoming ticketed events in Cornwall so they could afford to buy petrol to get home.
“Davina was upset, crying, and on the way home it was a quiet car journey,” Matthew said.
“I think we were both in shock – our holiday, that we go on once a year, has been ruined by someone who is probably doing this 10, 11 times a day, and you just think, ‘Why have they chosen us?’
“I was just thinking, ‘What could I have done better?’ You start to blame yourself.”
As he waited for updates from First Direct’s investigation, Matthew was feeling “concerned” and wondered: “How is this even possible? What else have they got access to?”
After a week, the £3,500 payment was refunded to his First Direct account, which was a huge “relief”, and Matthew said he was “impressed” with how the bank handled the case.
He was placed on a 12-month fraud prevention programme, which meant he had to go through “rigorous” processes when making large transactions, obtaining a loan or setting up a new account or credit card.
He said these processes sometimes took several hours, and although it was “frustrating” and some of his transactions were initially blocked, it made him feel “secure”.
“At the time, it was very frustrating to sit and do a million security questions… and trying to apply for things was a nightmare, but reflecting on this, I was grateful,” he said.
Matthew has since applied additional security measures to his accounts and changed email providers and his email address – but most importantly, he has set up two-factor authentication, which is something he did not have at the time of the scam.
However, even today hackers are still attempting to access his information through the email address he no longer uses.
“I have about six or seven notifications a day, saying, ‘Is this you? Confirm the number to get into your account’,” he said.
“I don’t use that email now and I deleted all my personal information off it, but I still have notifications coming from that email.”

Matthew has still not managed to do many of the things he had planned for the holiday, such as jet skiing, but he wants to share his story to encourage others to tighten their security measures on their devices.
“You just don’t think it’s going to happen to you until it happens,” he said.
“If I can educate at least one person – like my job as a teacher – then I’ve done my job.”
A First Direct spokesperson said: “Protecting our customers from fraud and scams is a key priority for us and we have a range of features in place to spot unusual activity on an account and protect our customers’ money.
“In this case, we’re really pleased we were able to intervene when Mr Shaw’s details were compromised and refund the money promptly.
“It is also standard practice for us to offer additional support to those customers who are victims of fraud, to give them extra assurances when making further payments so they feel confident and supported when managing their account.”

A Monese spokesperson said: “Here at Monese we take fraud extremely seriously, investing in and operating a range of controls to detect and prevent misuse of identities.
“These include algorithmic document authentication testing by specialist providers, identity confidence scoring, biometric matching of video selfies to the facial images in authenticated identity documents, and asking applicants to complete physical and verbal challenges, amongst other measures.
“As it stands, we can’t comment on this particular case as we don’t have enough identifying information to investigate. We’d love to contact Mr Shaw directly so that we can look into his case further.
“This would not only ensure that he receives the appropriate apology from us, but would also help us to protect other customers and thwart future fraud attempts.”