Fake Netflix app hijacked WhatsApp messages to spread malware on Android phones
The app claimed it would let users view global Netflix content, but instead messaged WhatsApp users to spread itself
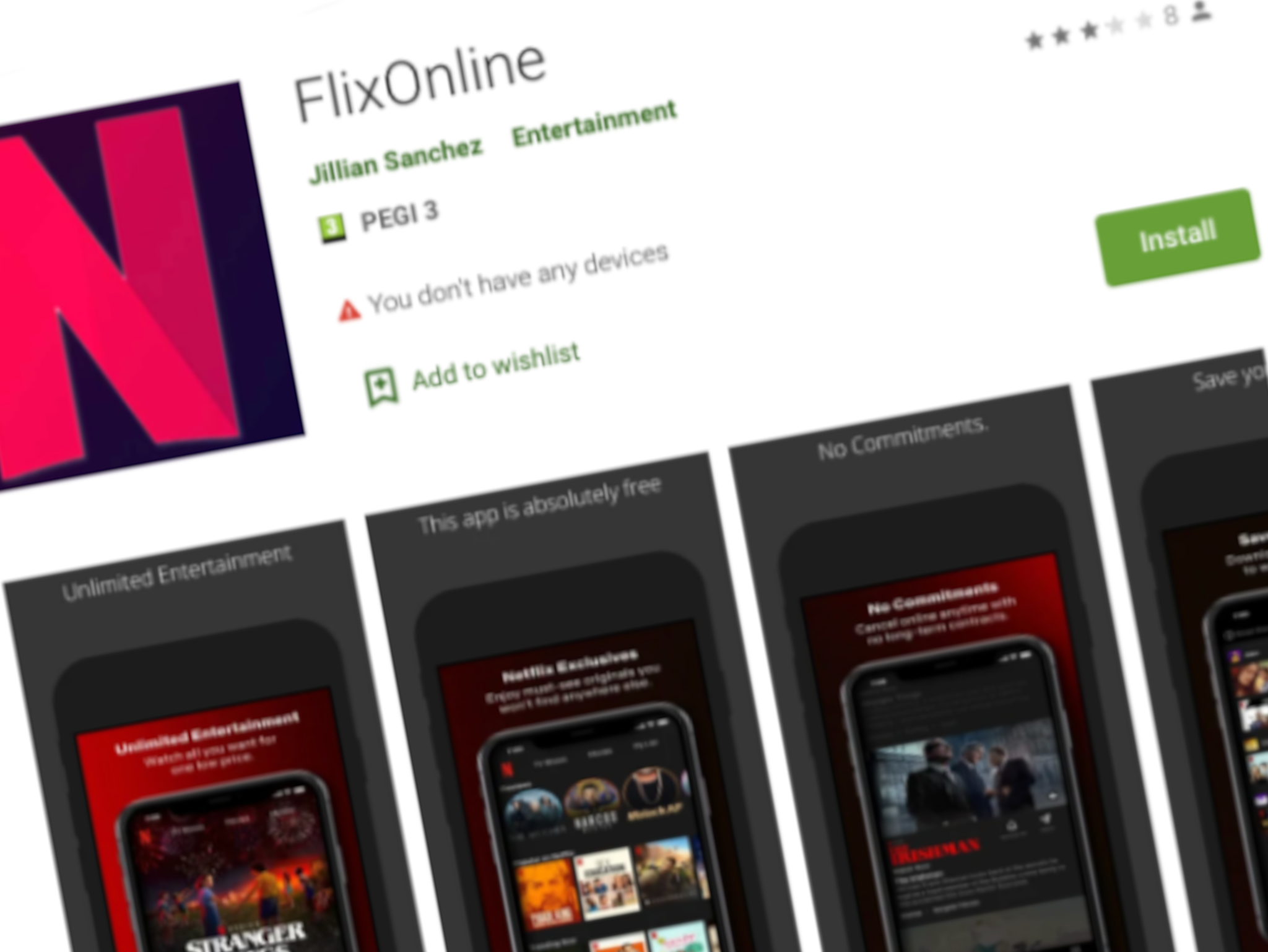
A fraudulent Netflix app which took control of users’ WhatsApp accounts has been spreading on Google’s Play Store.
The “FlixOnline” app claimed that it would let users access Netflix content from multiple regions on their phones.
Instead, it monitored the users’ WhatsApp notifications, sending automatically replies to the users messages telling them to sign up for FlixOnline.
“2 Months of Netflix Premium Free at no cost For REASON OF QUARANTINE (CORONA VIRUS)* Get 2 Months of Netflix Premium Free anywhere in the world for 60 days. Get it now HERE,” the message read, as discovered by Check Point Research (CPR).
Once a user had the app installed on their device, it could spread its malware further, steal data from WhatsApp and extort users by threatening to send sensitive data to all their contacts.
When the app was installed, users were asked for three types of permissions: screen overlay, battery optimisation ignore, and notifications. These allowed it to create a fake “login’ screen to steal credentials and allow it to reply to all incoming messages.
“After the permissions are granted, the malware displays a landing page it receives from the C&C [command and control] server and immediately hides its icon so the malware can’t be easily removed. This is done by a service that periodically contacts the C&C and updates the malware’s configuration accordingly,” Check Point Research explains.
A command and control server is a computer that issues directives to other devices which have been infected with malware.
“The service can achieve these goals by using multiple methods. For instance, the service can be triggered by the installation of the application and by an Alarm registered I the BOOT_COMPLETED action, which is called after the device has completed the boot process,” the researchers continue.
“The malware’s technique is new and innovative, aiming to hijack users’ WhatsApp account by capturing notifications, along with the ability to take predefined actions, like ‘dismiss’ or ‘reply’ via the Notification Manager,” Aviran Hazum, Manager of Mobile Intelligence at Check Point Software said.
“The fact that the malware was able to be disguised so easily and ultimately bypass Play Store’s protections raises some serious red flags. Although we stopped one campaign using this malware, the malware may return hidden in a different app.”
Google, when alerted to the existence of the app, removed it from its Play Store. Over the course of two months, Check Point Research says the app was downloaded approximately 500 times.
“Although apps like this are rare and infrequently downloaded, the threat they possess is huge – and this discovery could suggest the beginning of more malicious apps to come. Being able to send rogue messages from another app installed on a device is impressive and extremely dangerous, as when those messages appear on victim’s phones, they come with a sense of trust from a known contact. This is what makes this attack so highly effective and manipulative,” commented Jake Moore, Cybersecurity Specialist at ESET.
“Malicious actors know that worms like this work far better when passed on via contacts rather than unsolicited communication. If someone has downloaded this or a similar app, they may be sending WhatsApp messages out without realising, so people need to be remain cautious of links and attachments in received messages – even from known contacts.”
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments