Experts show how hackers withdraw wads of money from cash machines
Kaspersky Lab's Global Research and Analysis Team looked at ATMs across Eastern Europe and found that a piece of malware enabled them to get 40 notes in one go
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.Security experts have revealed how they managed to hack into a cash machine and order it to dispense wads of money.
Members of Kaspersky Lab's Global Research and Analysis Team, at the behest of a financial institution, said they undertook a “forensics investigation into a cyber-criminal attack targeting multiple ATMs in Eastern Europe” earlier this year.
Scroll down to see a video of how it's done
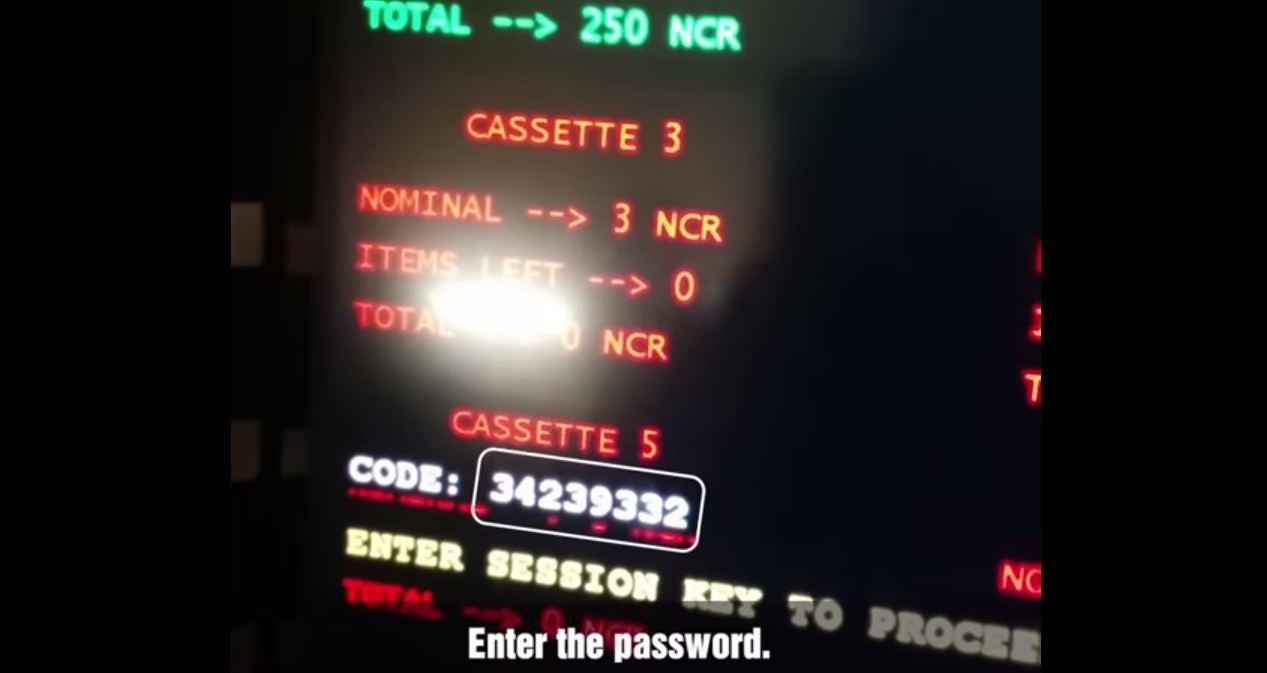
They found that a piece of malware on the machines called Backdoor.MSIL.Tyupkin – which at the time numbered at least 50 ATMs – allowed hackers to withdraw 40 notes without needing a debit or credit card.
The team believes that the malware has actually now spread from Eastern Europe to financial institutions in the US, France, China and India.
“The malware uses several sneaky techniques to avoid detection,” the team said in a blog post.
“First of all, it is only active at a specific time at night. It also uses a key based on a random seed for every session. Without this key, nobody can interact with the infected ATM.
“When the key is entered correctly, the malware displays information on how much money is available in every cassette and allows an attacker with physical access to the ATM to withdraw 40 notes from the selected cassette.”
It is believed that the cyber attackers were able to install the malware via a bootable CD.
A YouTube video showing how the experts managed to overcome the system has been posted online.
Kaspersky Labs said increased public and official awareness on card skimming operations by fraudsters had meant that they had to adapt and try new ways of targeting the cash machines.
According to the BBC, Interpol has alerted countries that may have been affected and is conducting an investigation.
At the end of their explanation, the experts wrote a list of recommendations for businesses, including making sure the ATM security alarm actually works because the hackers appeared to have targeted ones whose alarms didn’t.
“Ensure the ATM is in an open, well-lit environment that is monitored by visible security cameras. The ATM should be securely fixed to the floor with an anti-lasso device that will deter criminals,” they said.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments