New Android exploit lets hackers steal passwords with hidden on-screen tricks
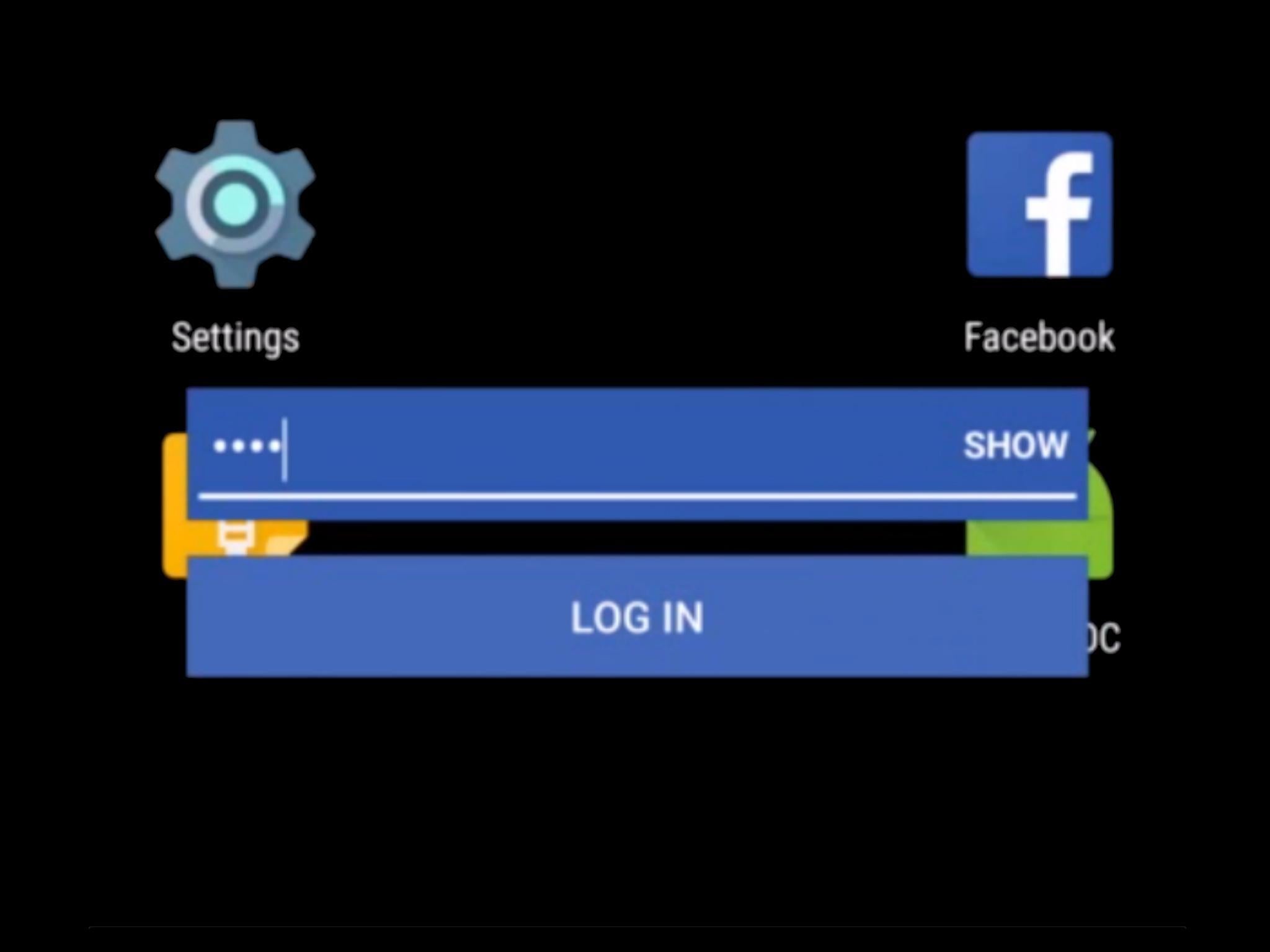
In one case, they created an overlay that looks exactly like the Facebook app’s password entry field
Researchers have discovered a new exploit that could let hackers secretly hijack your phone while you’re using it.
They successfully carried out proof of concept attacks on multiple versions of Android, up to the 7.1.2 build of Nougat.
Using the exploit, criminals can trick you into tapping buttons you can’t see, as well as record everything you do on your phone and collect important information, such as your passwords and PINs, without you even noticing.
Called Cloak and Dagger, it takes advantage of two permissions on the Android operating system: SYSTEM_ALERT_WINDOW (“draw on top”) and BIND_ACCESSIBILITY_SERVICE (“a11y”).
The “draw on top” permission lets apps display their content over other apps.
The research team, from UC Santa Barbara and Georgia Tech, took advantage of this functionality by building interactive overlays designed to look exactly like popular programs you wouldn’t usually think twice about entering your login details into.
In one case, they created an overlay that looks exactly like the Facebook app’s password entry field. If you failed to spot it, as many users would, you’d end up feeding your password directly to criminals.
In another instance, they created an invisible overlay that sat on top of the Android keyboard, which would be able to record every single thing you type.
“If the malicious app is installed from the Play Store, the user is not notified about the permissions and she does not need to explicitly grant them for the attacks to succeed. In fact, in this scenario, ‘draw on top’ is automatically granted,” the researchers say.
“Most of these attacks are due to design issues, and they are thus challenging to prevent. In fact, one may say that some of these functionality work "as intended"; Nonetheless, this work shows that this functionality can be abused.
To date, all these attacks are still practical.”
To protect yourself, you can check which applications have access to the "draw on top" and a11y permissions. The Cloak and Dagger researchers have compiled a list of instructions, which users on different versions of Android can follow.
“We’ve been in close touch with the researchers and, as always, we appreciate their efforts to help keep our users safer,” said Google.
“We have updated Google Play Protect — our security services on all Android devices with Google Play — to detect and prevent the installation of these apps. Prior to this report, we had already built new security protections into Android O that will further strengthen our protection from these issues moving forward.”
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
0Comments