Israeli army says Hamas militants ‘catfished’ soldiers with photo-sharing app to hack phones
Posing as young attractive women the militant group encouraged dozens of Israeli soldiers to download malware, the army says
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.Hamas militants, posing as attractive young women, have infected the mobile phones of dozens of Israeli soldiers, with malware embedded in fake photo-sharing apps, the Israeli military has said.
Lieutenant Colonel Jonathan Conricus, an army spokesman, said they have successfully thwarted the cyberattack, the third such attempt over the last three-and-a-half years.
This time the military said the attack was “more advanced and sophisticated” and infected more phones than the last effort in July 2018.
Over the last few months militants, who run the Gaza Strip, have attempted to woo soldiers on social media platforms including Telegram, WhatsApp, Facebook and Instagram.
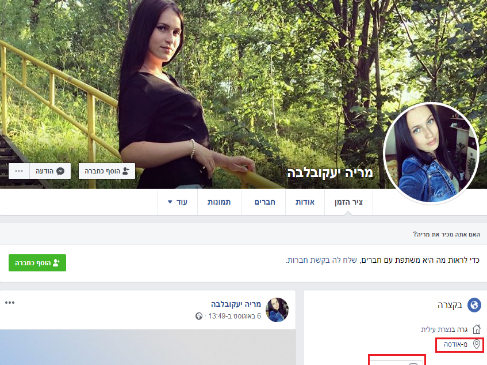
Using fake personas of attractive Israeli women, the militants behind the profiles claimed they were immigrants with hearing difficulties to explain why they could not speak on the phone, and why they were not fluent in Hebrew.
They also used Israeli slang in their communiques, doctored photos to prevent a reverse image search online and sent generic voice messages of women’s voices saying “yes” and “no” to further bolster credibility.
As soon as the apps were downloaded it gave Hamas complete control over the phone: including transferring files to the Hamas server, allowing access to the phone’s data, SMS messages, contacts, microphone and camera to remotely take pictures, Lt Col Conricus said.
He added that there was no “substantial breach of information” as they were able to catch the attack quickly.
“[We] have been able to, using technology tools, locate and thwart an attempt by Hamas to introduce malware into Israeli soldiers’ phones and by doing so collect intelligence,” Lt Col Conricus said on Sunday.
The attack was “more advanced and sophisticated” than last time he said, adding, “they are upping their game”.
“We do not expect there has seen any substantial breach of information … but we will continue to evaluate that,” he said.
The Israeli army later tweeted “What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.”
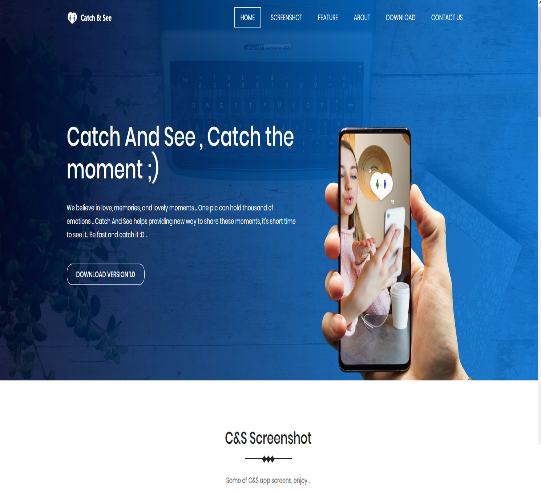
The army said that young – mostly male – soldiers were encouraged to download three applications containing malware called “Catch&See” “ZatuApp” and “GrixyApp” in order to exchange photos for a limited time, similar to SnapChat.
In screenshots of one conversation the military shared, a 20-year-old unnamed soldier downloaded “Catch&See” after a militant posing as a 21-year-old Israeli woman called Maria said she wanted to send him nude photos.
The soldier tried to open the app, but a message popped up saying it was not compatible with his phone, before the app deleted itself.
The malware, however, was still on the device allowing full control, the Israeli military said.
It followed a similar attack in July 2018 when Israel accused the militants of building two fake dating apps – WinkChat and GlanceLove – that also infected devices with malicious software.
During the same time militants also encouraged Israeli soldiers to download an app called “Golden Cup” which claimed it provided real-time information on the 2018 World Cup, the army said at the time.
The Israeli military said the militants usually approach young soldiers in active service who post photos of themselves in uniform online.
They said in this attack they identified six “characters” known as Sarah Orlova, Maria Ya’akovleva, Eden Ben Ezra, Noa Danon, Yael Azoulay and Rebeca Abuksis.
It is not yet known how many soldiers were approached in total or how senior they were.
Over the last few years, Hamas has increased its attempts at cyber warfare specifically targeting young Israeli military personnel.
Hamas has fought three wars with Israel since 2008.
Over the last year, tensions have reached breaking point, as there have been numerous exchanges of cross-border fire. Most recently in November, Gaza fighters fired hundreds of rockets into southern Israel and Israel pounded hundreds of sites in the Strip.
Gaza, home to two million people, has been crippled by a 13-year Israeli and Egyptian siege imposed after Hamas seized control of Gaza after winning elections in 2007.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments