Centcom 'hacked' by Isis supporters: US military Twitter feed publishes personal information of senior officers
Twitter feed posting details of senior officers and officials

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.A US military Twitter feed appears to have been hacked by people claiming to be sympathisers of the Isis militant group.
In a disturbing demonstration of the vulnerability of the American government’s cyber networks, a group claiming association with Isis gate-crashed the Twitter account of Central Command, also known as CentCom, and began posting internal information including personal details of senior officers.
Identifying themselves as the Cyber Caliphate, the infiltrators seized Central Command’s Twitter account at about 12.30 pm eastern time on Monday and began posting assorted messages including threats to US military personnel. They said the hacking operation was part of a so-called ‘CyberJihad’.
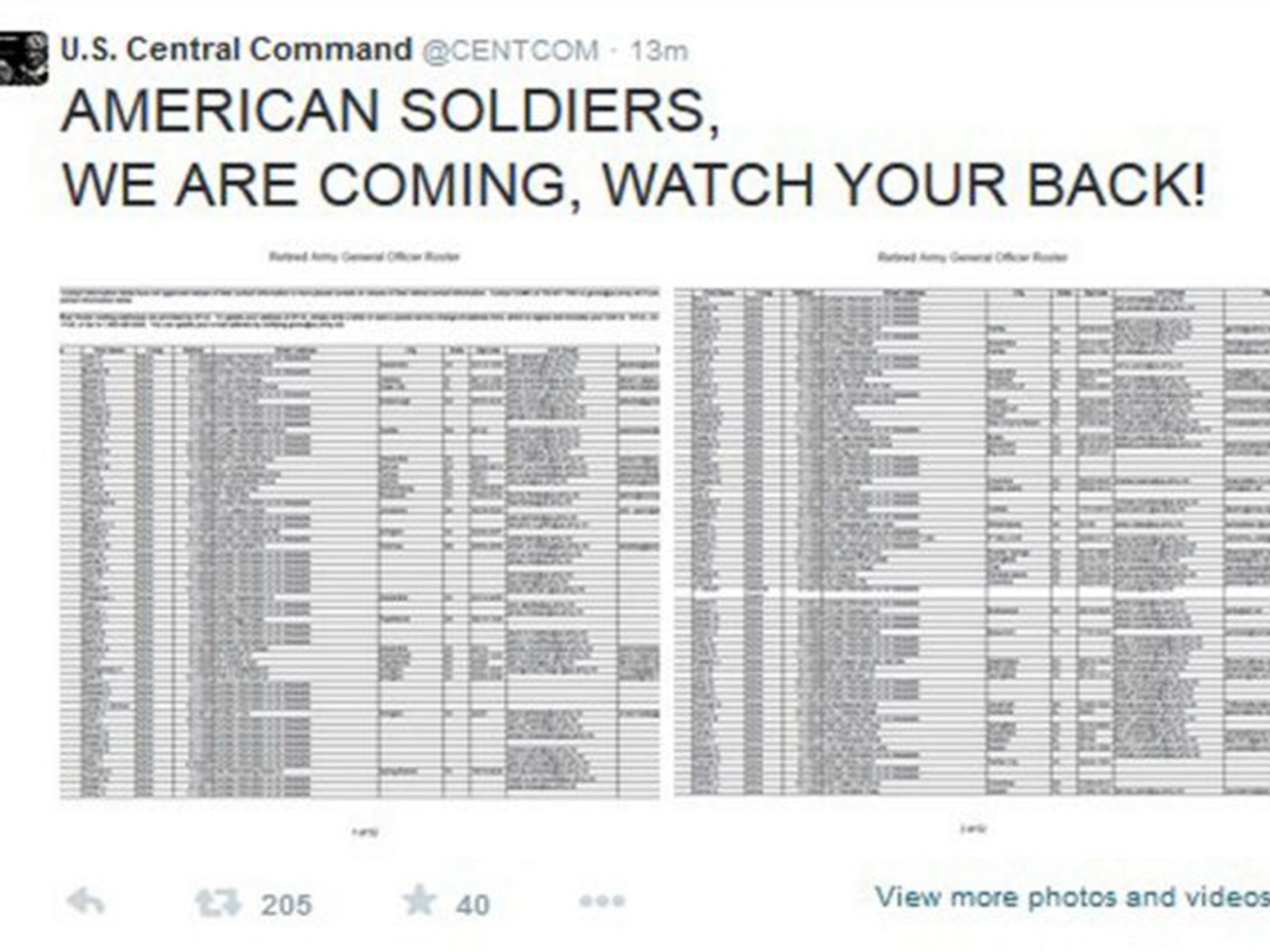
Among messages seen by anyone following the account was, “AMERICAN SOLDIERS, WE ARE COMING, WATCH YOUR BACK. ISIS”. As well as posting direct messages and threats, the group used the incursion to post images of documents containing what appeared to be sensitive Pentagon information as well as links to other sites where more information was available for download.
However it wasn’t clear if those documents had been stolen as a result of an earlier, successful hack into Pentagon servers or if they were in fact already publicly available. A US Defence Department official told Reuters that nothing in the trove of information being made available was classified.
Showing a degree of sophistication that will nonetheless sound alarm bells not just in Washington but in the capitals of all of America’s allies, including London, the group similarly changed the normal Central Command identifying picture to show instead a cover photo of a hooded man.
“You'll see no mercy infidels. ISIS is already here, we are in your PCs, in each military base. With Allah's permission we are in CENTCOM now,” the document reads. “We won't stop! We know everything about you, your wives and children. U.S. soldiers! We're watching you!”
A Pentagon official told NBC News that while the breach was certainly an embarrassment to the US government, it was “not a security threat”. Separately a US Defence Department official confirmed that Centcom’s Twitter account, which is to provide updates on coalition airstrikes on Isis positions, had been compromised. “Centcom is taking appropriate measures to address the matter,” he said.
Among the information displayed during the breach of the Twitter feed were the addresses, phone numbers and email addresses of retired and serving US Army generals. Also appearing on the feed were military details, apparently classified, regarding China and North Korea, including purported intelligence on current Chinese military operations and positions.
In all the breach is thought to have lasted for slightly less than 40 minutes before the account was suspended.
Centcom is the military command structure that oversees all US military operations in Afghanistan, Iraq and all across the Middle East, North Africa and Central Asia. It is housed within the grounds of MacDill Air Force just outside Tampa, Florida. President Barack Obama visited the base on 17 September on a mission to support the effort to counter Isis advances in Syria and Iraq from the air.
As officials in the Pentagon and the National Security Administration, which has its own cyber response headquarters at Fort Meade in Maryland, rushed to close down the incursion, it also emerged that the hackers had similarly taken control of Centom’s YouTube account and had begun posting Isis propaganda videos. One was called ‘Flames of War’ and another ‘O Solders of Truth Go Forth’. The YouTube account had also been closed down last night.
It wasn’t the first time the authorities in the US had seen of the group’s cyber handiwork. Last week, they successfully hacked into the Twitter page of the Albuquerque Journal in New Mexico as well as a Maryland television station, WBOC-TV.
The Independent called the number listed for General Daniel Allyn, commander of US Armed Forces. A woman answered, she said it was the office for Lieutenant General Patrick Donahue, Deputy Commanding General of the US Armed Forces. Gen Donahue was not available, she said. Told that the office telephone number was available online, she said: “So the numbers are on the CentCom twitter? I’ll pass it on to communications who will look in to it.”
Only yesterday, President Barack Obama told staff at the Federal Trade Commission in Washington DC that the US needed to do more to protect against cyber incursions and step up cyber security arrangements while citing the recent hack attack against Sony’s Hollywood film studio.
“If we're going to be connected, then we need to be protected,” he said.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments