Russian-speaking countries pose 'number-one cyber threat to UK', officials warn
Billions of pounds have been lost so far in the UK as attacks continue to hit every day

Russian-speaking countries pose the “number one cyber crime threat to the UK” as billions of pounds are lost in daily attacks, it has been revealed.
Senior police and intelligence officials warned of an increasing crossover between hostile states and criminal groups seeking to profit from targeting governments, national infrastructure, businesses and individuals.
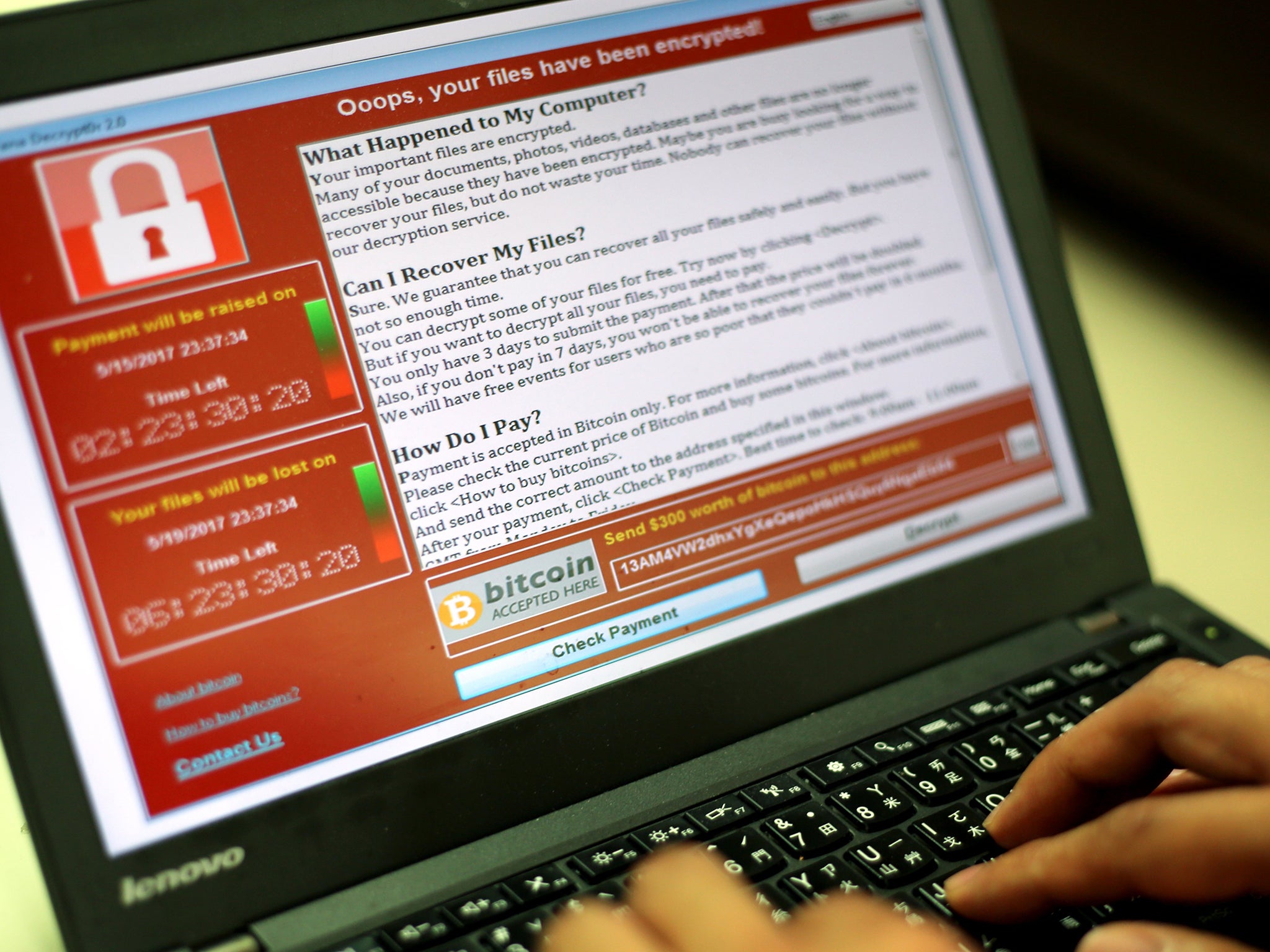
They warned that attacks as severe as the WannaCry ransomware outbreak, which crippled the NHS by hitting 81 trusts and affecting 19,000 appointments, could happen again.
“WannaCry is not going to be the last attack to hit the UK and things are likely to get worse before they get better,” said Oliver Gower, head of the National Cyber Crime Unit. “State actors have tried and will try again to target the UK.
“We also know that terrorists show the intent to use cyber attacks to cause damage and spread fear, but we don’t yet believe they have the capability to launch major attacks.”
Speaking in central London, he declined to confirm claims North Korea was behind the global WannaCry attack and said the investigation was ongoing.
An undisclosed number of Russian citizens have been arrested in relation to attacks on the UK and more than 100 investigations have been launched this year.
“Russian-speaking nations are the number one cyber crime threat to the UK,” Mr Gower said. “The available intelligence suggests a degree of crossover between state and criminal cyber actors.
“With innovative criminal capability available to the highest bidder, it is inevitable that hostile states will explore its possibilities, and conversely that very entrepreneurial cyber criminals may seek to steal data in order to sell to states.”
Officials stressed that WannaCry and similar attacks make up only a small fraction of cyber crime, which includes hacking, data theft and distributed denial-of-service (DDoS) attacks.
They pointed to the NotPetya ransomware impact on global shipping giant Maersk, which was forced to halt some operations, as an example of the “chaos” that future outbreaks could cause.
Mr Gower, who is also deputy director of the National Crime Agency (NCA), said tens of millions of cyber attacks have hit the UK, which are affecting people daily as new attempts are launched and malicious software continues to circulate.
The cost of cyber attacks in Britain is estimated to be in the “low billions”, comprising money stolen from individuals and businesses, and the funds needed to repair damaged systems and install increased protections.
Hairdressers, a radio station, and a solicitors firm are among the British companies suffering financial losses and there are fears of “real-world harm”, such as that seen from power outages caused by cyber attacks in Ukraine.
Investigators say motives can range from pure profit to disruption and political pressure, depending on whether the culprits are hostile states, organised crime gangs, lone hackers, ideological “hacktivist” groups or script kiddies looking for kudos among their peers.
With increasingly blurred lines between criminal and state actors, and single attacks using perpetrators and infrastructure across multiple countries, identifying a source is difficult and can involve international investigations.
The culprits behind an unprecedented series of high-profile attacks to hit Britain this year have not been officially named, although Iran was reportedly linked to a “brute force” assault on Parliament’s email systems in June.
The attack, described as “sustained and determined” by investigators, affected 9,000 email accounts and was followed by a similar incident targeting the Scottish Parliament.
Separately, Russian hackers have attacked Britain’s energy networks, telecommunications and media in what the head of the National Cyber Security Centre (NCSC) called an effort to “undermine the international system”.
On Monday, Theresa May accused Russia of “threatening the international order” with alleged interference in foreign elections, fake news and cyber attacks.
The Prime Minister said the UK would do “what is necessary to protect ourselves” and allies from disruption from Moscow, urging Vladimir Putin to step back from the “sustained campaign of cyber espionage and disruption”.
Mr Putin has repeatedly denied state involvement in cyber attacks and electoral influence, although he claimed “patriotically minded” Russian hackers may have launched their own attempts.
Security officials say hostile states often leave room for denial by employing criminal groups for hacking operations, or merely “permitting” their operations where their aims are mutually beneficial.
Mr Gower said culprits are “not as anonymous and unreachable as they think they are” but that the reporting of cyber attacks needed to improve for authorities to gain a better understanding of the threat.
Of the 1.8 million cyber-dependent crimes that took place last year, according to the Crime Survey for England and Wales, only about 30,000 were reported to the dedicated Action Fraud unit.
Officials believe some members of the public are going to banks over identity theft or funds stolen online, rather than the police, and that businesses may fear damage to their reputation.
Chief constable Peter Goodman, the National Police Chiefs’ Council (NPCC) lead for cyber crime said it was the “fastest-growing, most complex, difficult form of volume crime we’ve ever seen”.
“The complexity is going up and the ability of victims to protect themselves is diminishing,” he warned, calling the current police response a “postcode lottery” as new regional teams are rolled out.
Ranked as a tier one national security threat alongside terrorism and organised crime, the danger posed by cyber criminals is expected to grow amid an explosion of internet-connected gadgets sold with little or no security.
A fish tank and kettle are among the “internet of things” items used to infiltrate systems by hackers and Mr Goodman called for new laws to ensure all hardware sold is fitted with a minimum standard of protection against cyber attacks.
While the news has been dominated by high-profile international incidents, the senior officer cautioned that small and medium-sized businesses “can’t survive” criminal attacks.
The NCSC, NPCC and NCA are all running public information campaigns aimed to help companies and members of the public protect themselves, while the new General Data Protection Regulation will force businesses to disclose data breaches from when it comes into force in May.
Mr Gower said it was time for all sectors to wake up to the threat posed by cyber attacks and urgently shore up vulnerabilities – like the outdated Windows operating systems that allowed WannaCry to spread so rapidly through the NHS.
“There’s a tendency to think of this threat as some sort of faraway, abstract thing but it’s not,” he warned.
“Hacking, data theft, ransomware, DDoS – these are the modern equivalents of traditional crimes, except that they’re not limited by the geography and physics of the real world.”
