Hacker who blackmailed porn users into handing him money after they clicked on his pop-up adverts jailed
Student was part of international Russian-speaking organised crime group that made millions from victims around the world
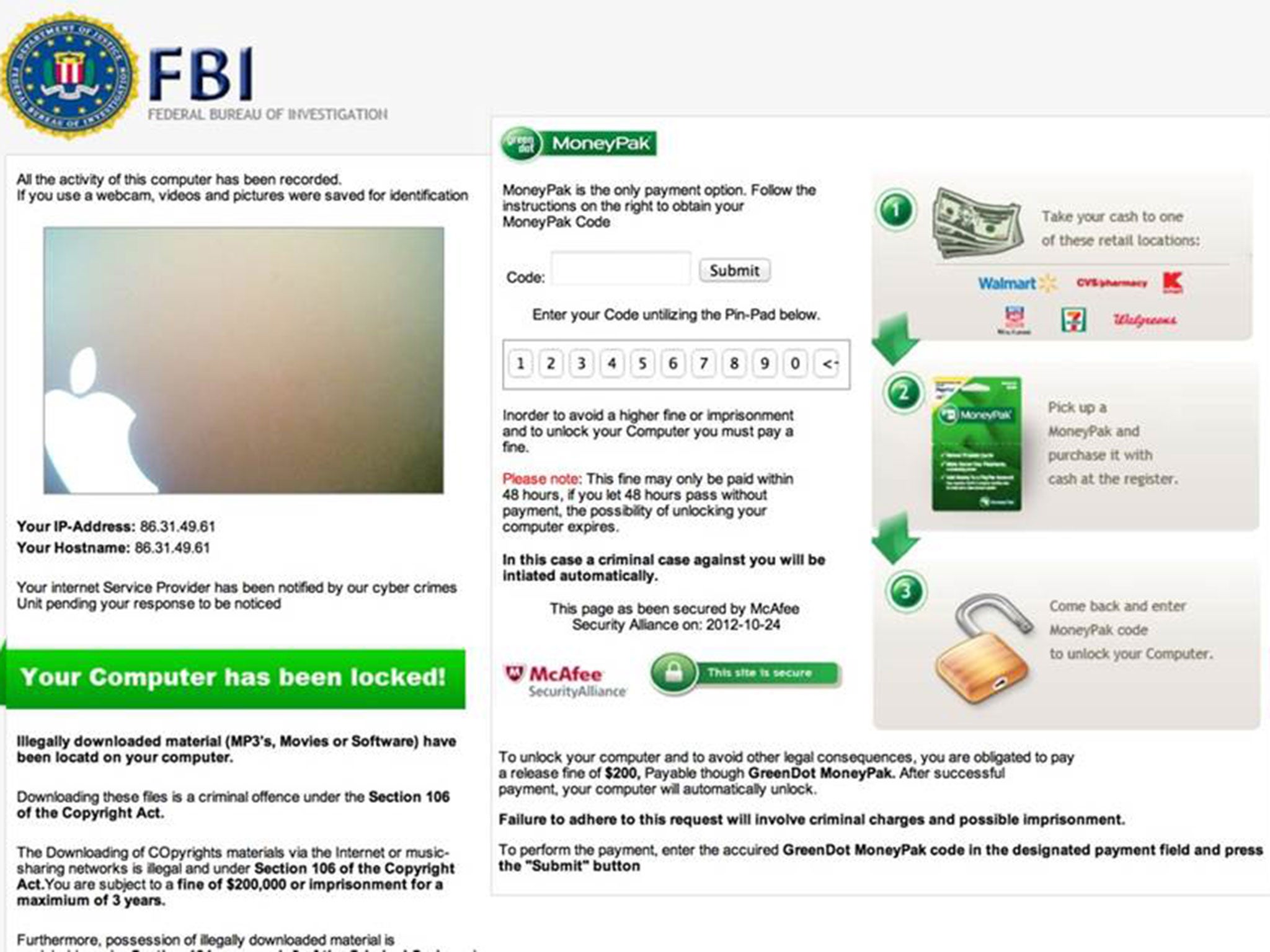
A hacker who made more than £700,000 by locking porn users' computers and blackmailing them has been jailed.
Zain Qaiser, 24, targeted millions of computers with pop-up adverts that triggered ransomware threatening browsers with prosecution unless they paid a “fine”.
Kingston Crown Court heard that messages displayed on frozen screens impersonated law enforcement in the user's country, and demanded payments of up to $1,000 (£767).
Qaiser was jailed for six years and five months after admitting blackmail, fraud by false representation, hacking and possessing criminal property.
Passing sentence on Tuesday, Judge Timothy Lamb QC said: “The harm caused by your offending was extensive - so extensive that there does not appear to be a reported case involving anything comparable.
"Whatever your motivation for mounting these attacks on the internet you took the opportunity to spend large sums of ill-gotten money in casinos, on an expensive watch and luxury hotel services.
“All the constituent offences were part and parcel of your role as the self-styled 'K!NG' of the internet.
"It has been asserted on your behalf you are remorseful. I have seen no outward expression of that."
The former computer science student, who committed most of his crimes between the age of 18 and 19, remained expressionless as the sentence was passed.
Prosecutors said Qaiser was part of a Russian-speaking “sophisticated organised crime group” and used a series of false identities to commit his crimes.
The Crown Prosecution Service (CPS) intends to initiate legal proceedings to confiscate almost £116,000 of “criminal money”, which Qaiser admitted receiving while he was on bail.
Prosecutors believe Qaiser was paid a “far higher” amount than the £700,000 traced between September 2012 and his arrest in 2014, and suspect he has money hidden in offshore accounts.
Despite being a student with no apparent source of income, he visited prostitutes, gambled nearly £70,000 with his Asper’s casino account and purchased a £4,900 Rolex watch, the court heard.

The National Crime Agency (NCA) said the total profit made by the group he worked with runs into the millions, from victims in more than 20 counties.
Qaiser, a former City University student from Barking in east London, bought masses of advertising space using the online name K!NG.
Using fraudulent identities and bogus companies to pose as legitimate online advertising agencies, he then posted advertisements laced with malicious software.
When users clicked on the ads they were redirected to another website, hosting highly-sophisticated malware strains that would infect unprotected computers and lock them down with the ransomware message.
Blackmailed victims would be directed to pay the ransom demand using a prescribed virtual currency, which would then be laundered using a variety of methods and an international network of illegitimate financial service providers.
Millions of computers were targeted with the messages purporting to be from a government agency or police department in their home countries between 2012 and 2014.
Prosecutors said that despite not having committed a crime, many victims paid up out of embarrassment.
Some advertisers were "happy to turn a blind eye" to Qaiser's actions - but those who tried to stop him "became the subject of the defendant's anger", prosecutor Joel Smith told the court.
He told one advertising director “I’ll first kill your server, then send child porn spam abuses” if they refused to allow his pop-ups on the porn sites.
Where they did not comply, Qaiser launched distributed denial of service attacks, which shut down companies’ systems and cost them at least £500,000 through lost revenue and mitigation costs.
Russell Tyner, of the CPS Organised Crime Division, said: “This was no amateur operation. Zain Qaiser is a member of a prolific and technically sophisticated international criminal organisation that has terrorised internet users throughout the world.
“While he enjoyed an extravagant lifestyle on the proceeds, Qaiser subjected his victims to a prolonged and relentless campaign of blackmail, which caused them significant financial and emotional harm.”
A search of Qaiser’s computer after he was arrested in July 2014 found more than 3,000 online chat logs.
Qaiser was charged in February 2017, but a trial set for February 2018 was abandoned when he was sectioned under the Mental Health Act.
While he was detained at Goodmayes Hospital in north London, the hospital Wi-Fi was used to access online advertising websites Qaiser had used for his offending, the court heard.
He initially denied the crimes and claimed he had been hacked himself, but later entered guilty pleas to an 11-count indictment.
Mr Tyner said the CPS had worked with the NCA and law enforcement in Canada, the US and Europe to build the case, adding: “Many cyber criminals believe they are too clever to be caught by the law but this conviction demonstrates we have the expertise to bring these offenders to justice.”
Nigel Leary, NCA senior investigating officer, said it was “one of the most sophisticated, serious and organised cybercrime groups” ever investigated.
“The group owned and operated the Angler Exploit Kit – one of the most successful and closely guarded pieces of malicious software ever developed by the cybercrime community,” he added.
“The FBI and the US Secret Service have both arrested people in relation to this global malware campaign.”
