Cloud misconfigurations on the rise: 2021 Cloud Security Report
THE ARTICLES ON THESE PAGES ARE PRODUCED BY BUSINESS REPORTER, WHICH TAKES SOLE RESPONSIBILITY FOR THE CONTENTS


Insufficient access restrictions, permissive storage policies and publicly exposed assets are only a few of the mistakes companies make when configuring their cloud infrastructure. The scale of the problem is mind-blowing, with 90 per cent of organisations vulnerable to security breaches due to cloud misconfigurations. Aqua’s Cloud Security Report sheds light on the most common cloud configuration issues in real production environments.
Uncovering cloud configuration risks
With cloud adoption accelerating at a rapid pace, organisations are overwhelmed with the sheer number of configurations to take care of. Even one service will involve users, roles and permissions, as well as varying default connections with other services that can be turned on or off. Each of those configurations will come with certain consequences to an organisation’s overall security posture.
The complexity of the environment is constantly intensifying, too – companies are expanding their cloud footprint, going hybrid and multi-cloud, and adopting newly released services.
Over 12 months, our research team analysed anonymised cloud infrastructure data from real production environments across hundreds of organisations. The 2021 Cloud Security Report: Cloud Configuration Risks Exposed provides insights to help organisations better understand the risks that come with the move to multi-cloud environments as well as recommendations on best practices to mitigate them.
So, what are the key takeaways from the report?
Organisations need to fix security issues faster
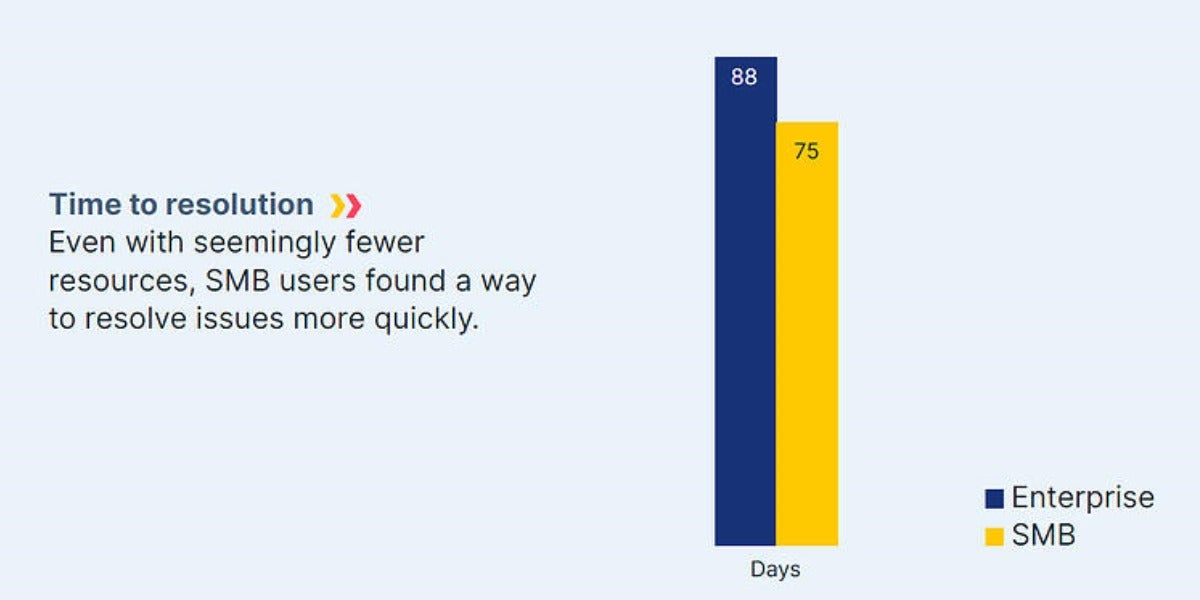
The majority of organisations fail to fix cloud misconfiguration issues in a timely manner. With the growing cloud footprint, it’s easy to be overwhelmed by the endless number of security issues being identified – especially if you’re a large enterprise. In our research, small and medium-sized businesses averaged about 75 days to remediate or resolve their configuration issues after discovery, compared to an average of 88 days for larger organisations:
Storage misconfigurations are still a major problem
Cloud storage buckets continue to attract a lot of attention due to high-profile breaches hitting headlines on a regular basis. Usually, this happens when the administrator managing the service misconfigured some security settings, leaving it open to the public. Of the environments examined, 82 per cent had “open to the internet” issues, making the organisations susceptible to breaches.
Credential hygiene requires more attention
While malicious actors are constantly reinventing their techniques to obtain cloud credentials, 74 per cent of organisations analysed aren’t practising credentials rotation and most of them had at least one issue with unused credentials.
Widespread cloud misconfiguration issues also affect Docker containers and Kubernetes
Adversaries are increasingly looking to exploit vulnerable container-related services in order to get initial access to your environment.
The report finds more than 40 per cent of users had at least one misconfigured Docker application programming interface (API) that took, on average, 65 days to remediate. On the Kubernetes front, a few users with ACL or network policy issues were found. Most of those issues were remediated within 65 days on average.

Conclusion
Cloud infrastructure is complex and difficult to configure properly, and a single misconfiguration of cloud settings can lead to serious problems. The good news is that 84 per cent of users reported that they were able to detect and remediate misconfiguration issues using a Cloud Security Posture Management solution, which automates the tracking and fixing of security risks across multiple clouds.
For complete findings and best practices on cloud configurations, download the 2021 Cloud Security Report
Originally published on Business Reporter