Android security flaw: More than 1bn phones could be hacked with single text message
Samsung, Huawei, LG and Sony smartphones vulnerable to attack

A major security flaw with Android mobile operating system has left over a billion Samsung, Huawei, LG and Sony smartphones vulnerable to cyber attacks.
Researchers at cyber security firm Check Point identified the bug in Android-based phones, revealing that it only takes a single SMS text message to gain full access to a person’s emails.
Around 2.5 billion devices around the world use the Google owned Android, which is the world’s most popular operating system. Any security issues therefore can have widespread consequences for users.
“Given the popularity of Android devices, this is a critical vulnerability that must be addressed,” said Slava Makkaveev, a security researcher at Check Point.
The Independent has contacted Google for comment.
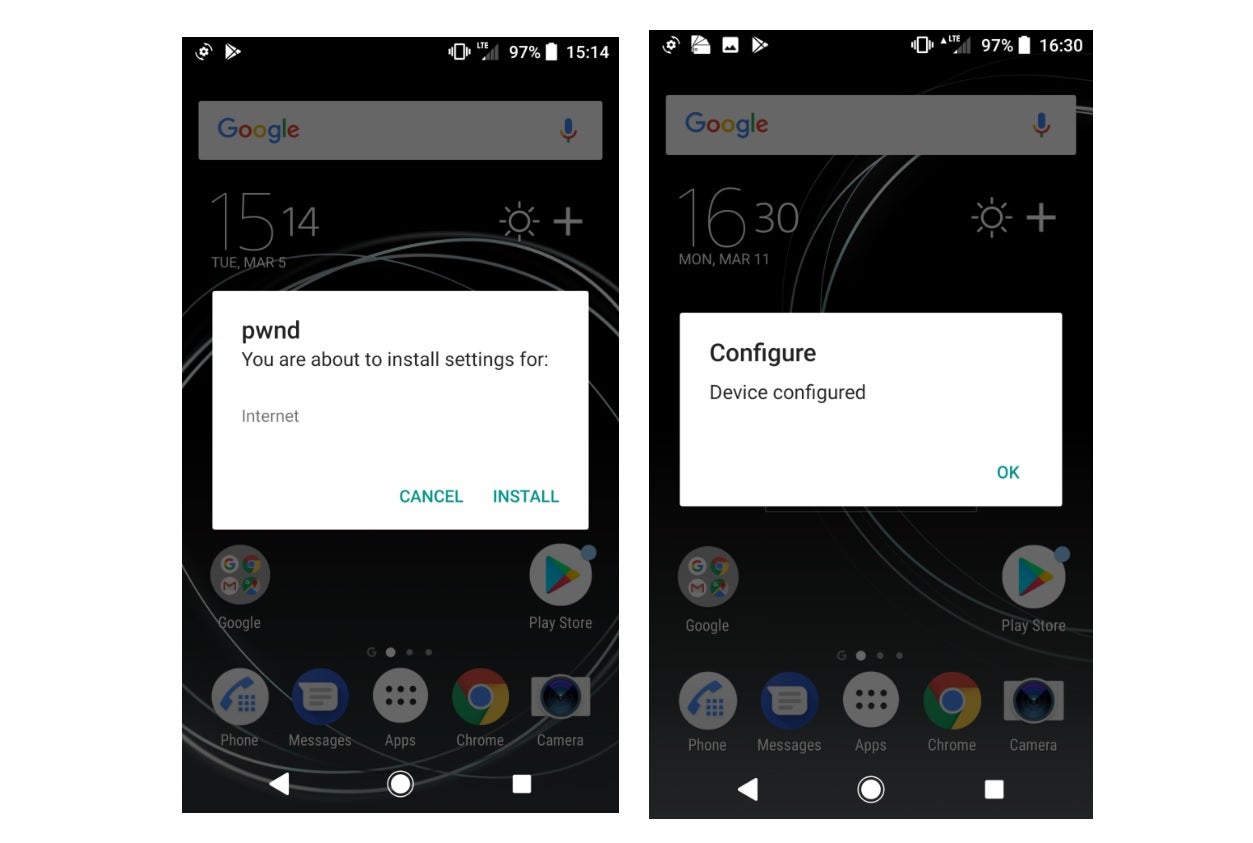
The hack works by making use of a technique that mobile network operators use to update new phones joining their network, known as an OMA CP message.
Check Point researchers found a lack of authentication checks allowed them to pose as network operators and trick users into accepting malicious settings through these messages.
One way of taking advantage of this vulnerability is by re-directing all internet traffic from someone’s phone through a proxy server owned by the hacker.
This would allow cyber criminals to view a person’s web history and read their emails.
“When the user receives an OMA CP message, they have no way to discern whether it is from a trusted source,” said Mr Makkaveev. “By clicking ‘accept’, they could very well be letting an attacker into their phone.”
The researchers said certain phones were more vulnerable to the attack, with the Samsung S9, Huawei P10, LG G6 and Sony Xperia XZ Premium all exposed when tested.
More than half of all Android smartphones could potentially be affected, though for the moment there is no evidence that it has been used beyond this proof-of-concept research.
All smartphone makers affected by the security flaw were informed about the research earlier this year and Samsung and LG have already issued fixes. The researchers said Huawei is planning to include a fix in a future update.
Check Point published further details in a blog post about how the vulnerability can be exploited and the tools needed to do so.
"This attack flow enables anyone who has a cheap USB modem to trick users into installing malicious settings onto their phones," the blog stated.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
0Comments