North Korea hackers could be behind NHS ransomware hack, say British security experts
National Cyber Security Centre says the North Korea-based Lazarus Group may have started the attack as a money-making scheme that got out of control
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
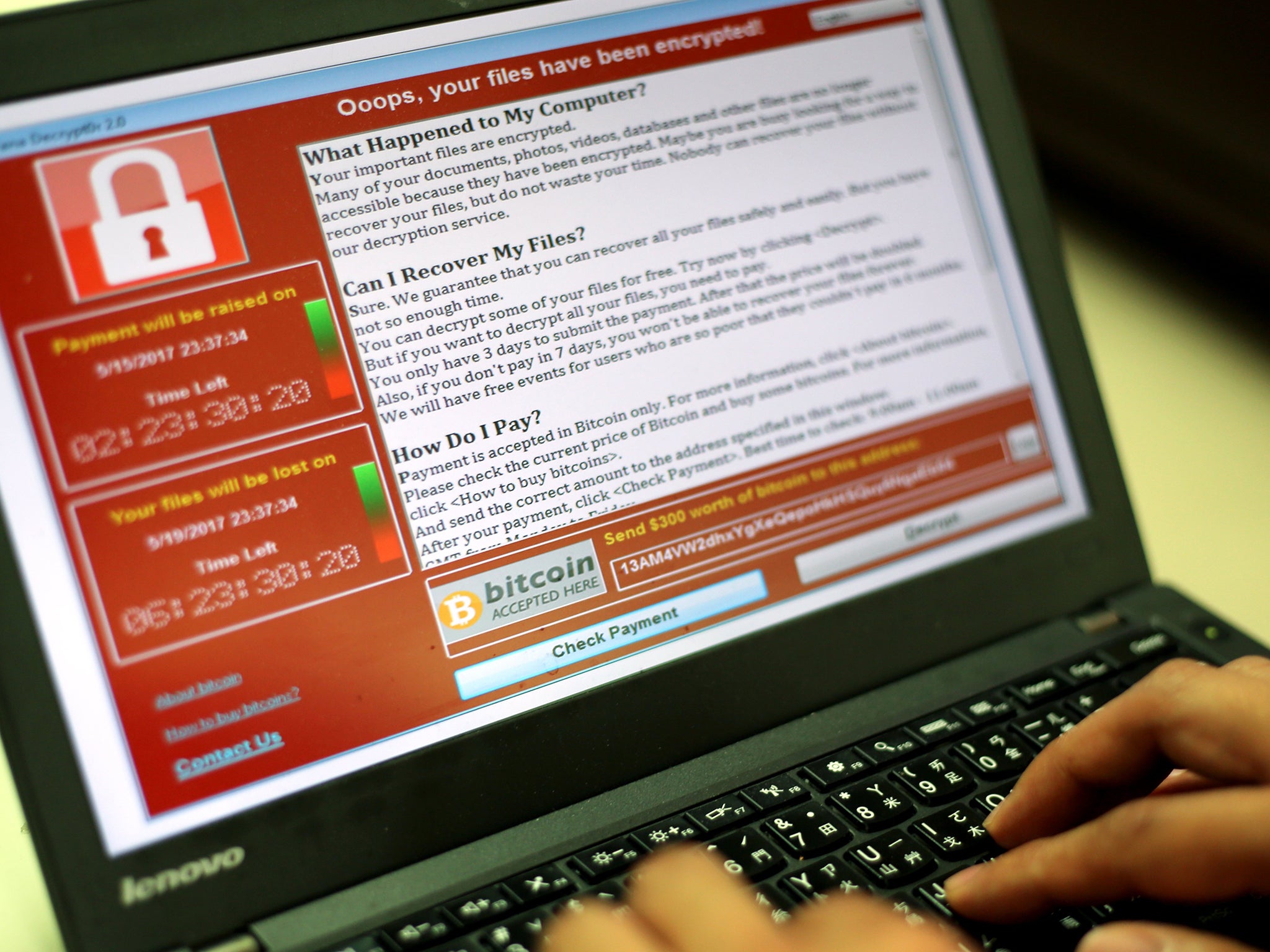
Your support makes all the difference.North Korean hackers may have been behind the WannaCry ransomware attack that crippled the NHS last month, British security experts have said.
The National Cyber Security Centre has led an international investigation into the attack, which is estimated to have affected more than 300,000 computers in over 150 countries worldwide.
Security sources at the government body told the BBC that a North Korean outfit called the Lazarus Group may have been behind the attack, which knocked out computer systems at 47 NHS trusts across the country last month.
Computers at the trusts showed a message saying their data had been encrypted and it would only be unlocked when they paid a ransom in bitcoins - a digital currency - into a specific account.
The hackers used a piece of software developed by the NSA spy agency in the US to exploit vulnerabilities in the out-of-date Windows XP operating system still widely in use across the NHS despite no longer being supported by manufacturer Microsoft.
It is believed that the attack would have been much worse had a British cyber-security researcher not discovered a secret “kill switch” in the code.
The NCSC concluded that the ransomware did not target Britain or the NHS specifically and may have been a money-making scheme that got out of control.
They highlighted the fact that the hackers have not yet retrieved the money they gathered from the attack as it may make them more vulnerable to detection.
The group, which has been operating out of North Korea for around a decade, is believed to have also been behind the Sony Pictures hack in 2014 and a raid on a Bangladeshi bank last year where hackers stole millions from several customers – including the Federal Reserve Bank of New York – in just minutes.
Adrian Nish, who leads the cyber threat intelligence team at BAE, told the Today programme that the group’s original aim seems to have been espionage but its focus, or at least a part of its focus, has shifted to money-making in recent years.
Although security researchers are keen to stress that they are not sure about the links between the Lazarus Group and the North Korean state, Pyongyang needs to find ways to raise foreign revenue as economic sanctions stop it using the normal means of raising foreign investment capital.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments