WannaCry: New tool can restore some ransomware-infected computers without paying up
There are a number of limitations, but WannaKey provides hope
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
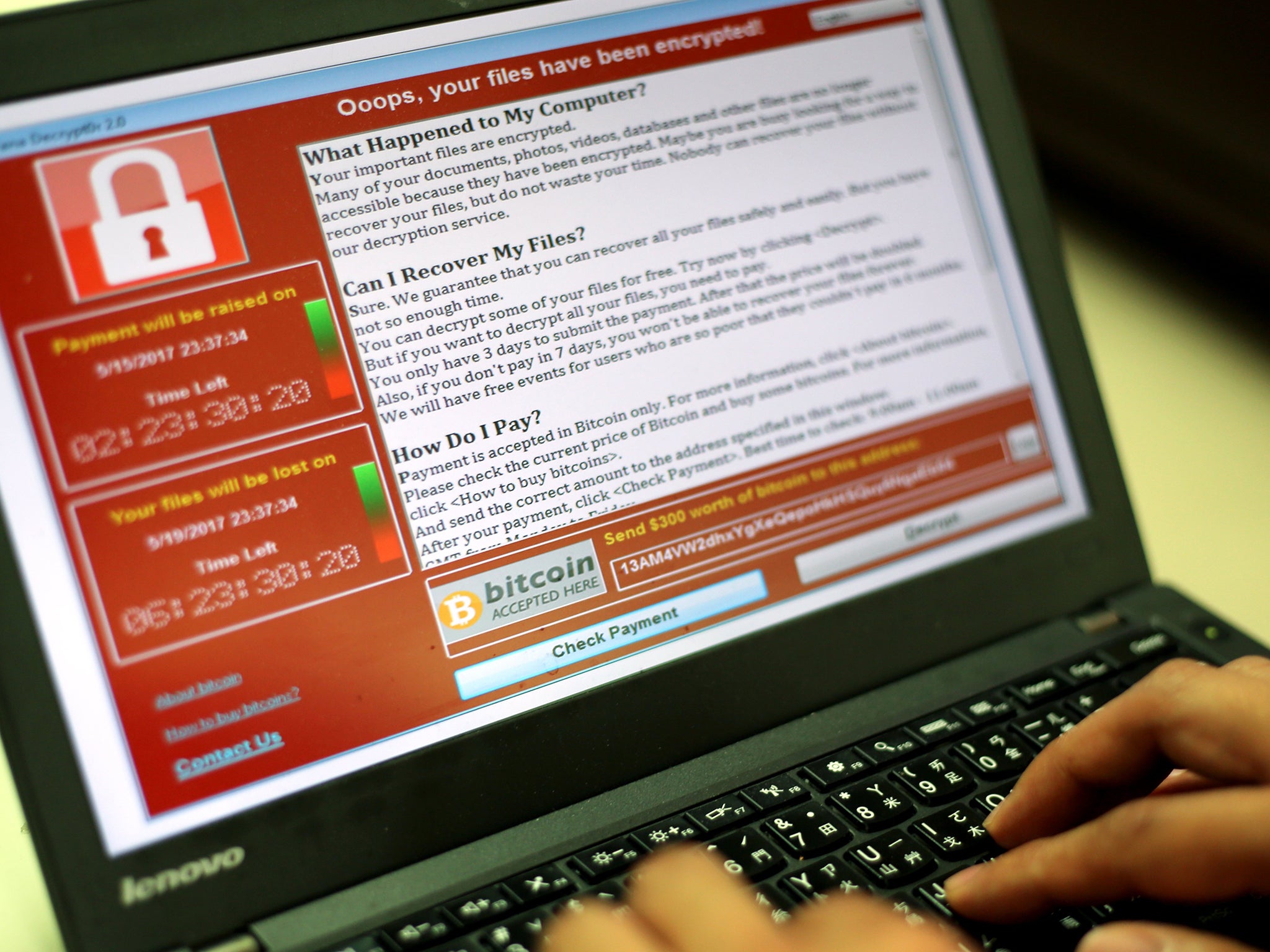
Your support makes all the difference.A security researcher claims to have created a new tool capable of restoring computers infected by WannaCry ransomware.
Adrien Guinet has released WannaKey, which is designed to take advantage of a shortcoming in Windows XP to decrypt an infected machine’s files.
He says he’s used it successfully on several infected Windows XP computers, but the method won’t work for all victims.
“In order to work, your computer must not have been rebooted after being infected,” says Mr Guinet, who adds that there’s also an element of luck involved.
“This software allows to recover the prime numbers of the RSA private key that are used by Wanacry,” he explains in a post on GitHub.
“The main issue is that the CryptDestroyKey and CryptReleaseContext does not erase the prime numbers from memory before freeing the associated memory. This is not really a mistake from the ransomware authors, as they properly use the Windows Crypto API. It can work under Windows XP because, in this version, CryptReleaseContext does not do the cleanup. ”
WannaKey won’t work on infected computers running Windows 10, Mr Guinet says, because CryptReleaseContext does clean up the memory on the platform.
“If you are lucky (that is the associated memory hasn't been reallocated and erased), these prime numbers might still be in memory.”
In an exchange on Twitter, Matthieu Suiche, another security researcher, said he also used the tool but it didn’t work for him. Still, Mr Guinet’s work provides some hope.
WannaCry is demanding a payment of $300-$600 from victims, but security researchers have warned users not to pay the ransom.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments