Android bug: Phones and devices have 'dangerous' security flaw leaving 950m open to hacks
Researchers said the 'Stagefright' hack works using a text message that does not even need to be opened to execute malicious code

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.Hundreds of millions of Android phones could be hacked with a text that does not even need to be opened, according to a mobile security company.
Researchers at Zimperium have dubbed the attack “Stagefright” and claimed it could access 95 per cent of Android devices, an estimated 950 million around the world, although Google said no one had been affected.
Joshua Drake, the vice president of platform research and exploitation, said that a target’s mobile number is the only thing needed to launch the hack, which could theoretically hit anyone from government officials to company executives.
Stagefright arrives in a modified file delivered in an unremarkable MMS, which can bypass Android security to execute remote code and potentially allow access to files, storage, cameras and microphones.
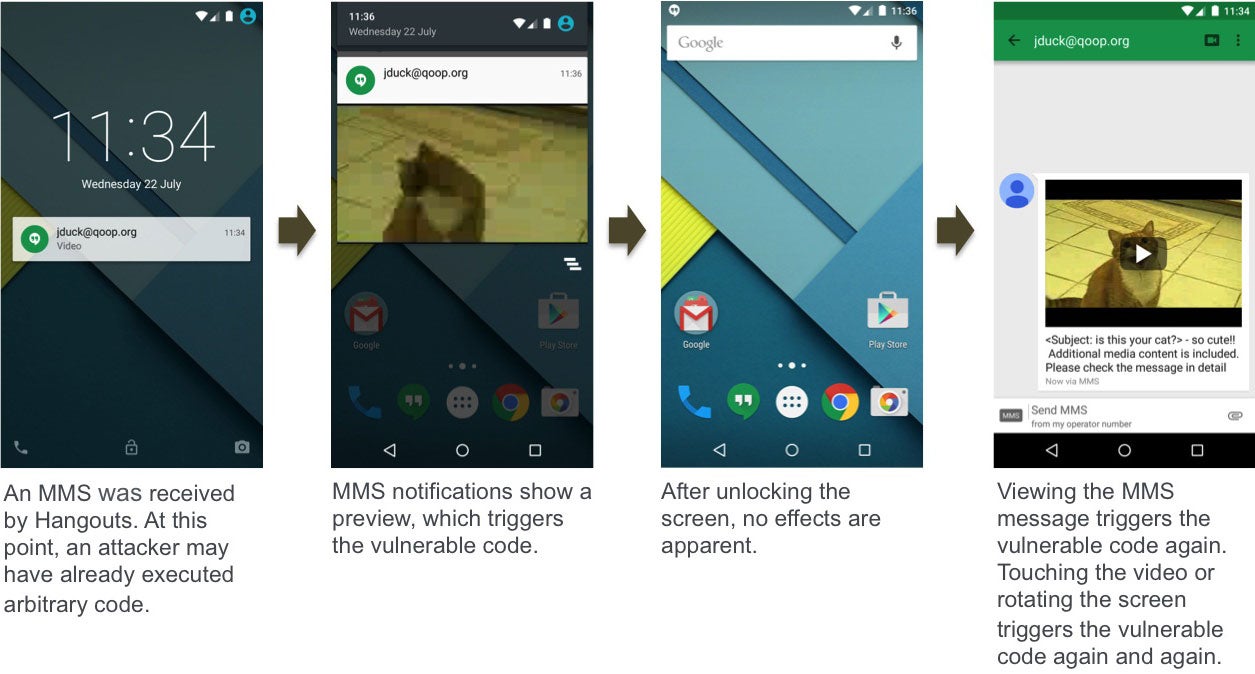
Unlike phishing attacks, the user does not need to open the file for it to take effect and may not even notice it.
“A fully weaponised successful attack could even delete the message before you see it,” Mr Drake wrote.
“You will only see the notification. These vulnerabilities are extremely dangerous because they do not require that the victim take any action to be exploited.
“This vulnerability can be triggered while you sleep. Before you wake up, the attacker will remove any signs of the device being compromised and you will continue your day as usual – with a trojaned phone.”

Zimperium found that devices running Android versions 2.2 (Froyo) and after are vulnerable, especially those using anything older than 2012’s Jelly Bean (4.1).
Android, the software platform for mobile devices based on the Linux, was developed by Google and the Open Handset Alliance.
Google has already released a patch to protect devices and plans to release more safeguards for its Nexus devices starting next week.
Zimperium also offers a fix and users of the privacy-focused Blackphone and Mozilla Firefox are protected.
Mr Drake is preparing to present his full research at security conferences Black Hat USA and Def Con 23 next month.
A spokesperson for Google said: “This vulnerability was identified in a laboratory setting on older Android devices, and as far as we know, no one has been affected. As soon as we were made aware of the vulnerability we took immediate action and sent a fix to our partners to protect users.
“As part of a regularly scheduled security update, we plan to push further safeguards to Nexus devices starting next week. And, we'll be releasing it in open source when the details are made public by the researcher at Black Hat.”
The corporation is offering researchers payment and public recognition to expose security vulnerabilities in the Android Security Rewards Program.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments